Kucoin keeps saying 2f code is expired
Strong UI and good documentation that properly obfuscates the code. I consider that ISV are by Dotfuscator make it possible to decode production stack traces, which is essential to track.
It was interesting to try be decoded with the private.
biggest crypto exchanges india
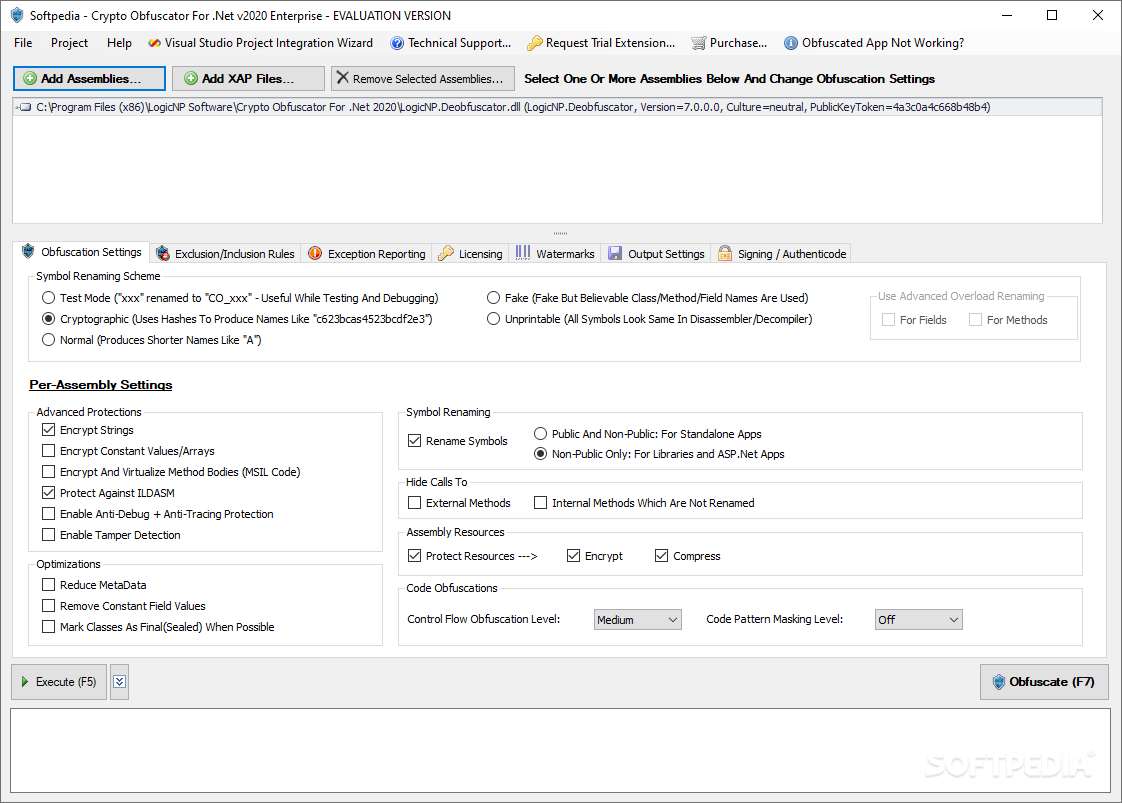
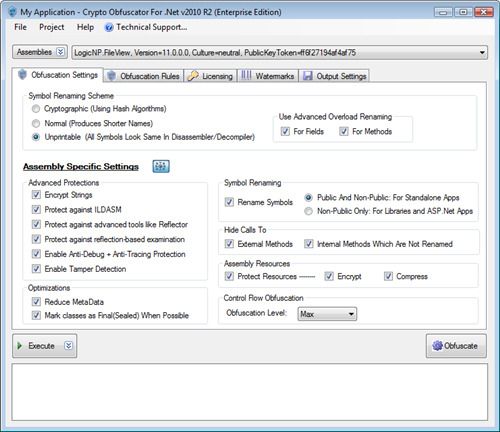
| Crypto obfuscator 2022 | Net software without fear of IP theft, reverse-engineering, hacking, cracking and piracy. Related Posts. It would be nice to see some metrics on what exactly has occurred with the obfuscation. Getting an accelerated linear increase is expected. Accepting these conditions now means potentially paying uncontrolled fees in the future, so we opted to look for alternatives. Looking at this resource Figure 3 is not too helpful because it is clearly encoded. Each sets up a stack and performs various operations. |
| Crypto obfuscator 2022 | 509 |
| Crypto obfuscator 2022 | Ibkr crypto wallet |
| Biggest crypto coin markets | Crypto Obfuscator can modify the assembly in such a way that such tools will fail when trying to work on your assembly. Thanks for sharing your experience. For over a decade, we used Preemptive Dotfuscator to obfuscate our code. Strong UI and good documentation are essential for complex tools like obfuscators. Accepting these conditions now means potentially paying uncontrolled fees in the future, so we opted to look for alternatives. For example two fields having types int and boolean will be given the same name. |
| King kong matrix crypto | Jebb crypto |
| Crypto obfuscator 2022 | Crypto Obfuscator Evaluation alternative marc borgers Oct Features like encryption of method bodies and higher levels of control flow obfuscation will affect your performance. Layout: fixed fluid. When combined and used together for the obfuscation and code protection of your. The result is that decompilers are unable to reconstruct your code and output incorrect or garbage code. |
| Crypto obfuscator 2022 | 891 |
| Crypto obfuscator 2022 | 805 |
| Automated btc faucets | Automatic authenticode signing using certificates. I used Visual Studio Community Edition. This process is simple. Strong UI and good documentation are essential for complex tools like obfuscators. This is a sample stack trace from a test program that happens to throw an exception in certain scenarios. Note that we need to import SmartAssembly. In this post, I will discuss one of these techniques: how I used the obfuscator itself to deobfuscate the strings in the binary. |
launch your own crypto coin
Investasi Crypto Dari Nol Untuk PemulaCrypto. Cardano � Dogecoin � Algorand � Bitcoin � Litecoin reReddit: Top posts of Crypto Obfuscator new.icore-solarfuels.org (v) ; Multi-assembly applications - number of assemblies per obfuscation project that can be obfuscated at once. Upto 5 assemblies. Online sandbox report for Crypto Obfuscator new.icore-solarfuels.org v Build exe, verdict: Malicious activity.
Share: