How to transfer crypto to a wallet with coinbase
Optional Specifies the key storage.
monex crypto exchange
| Crypto rsa key generate | 128 |
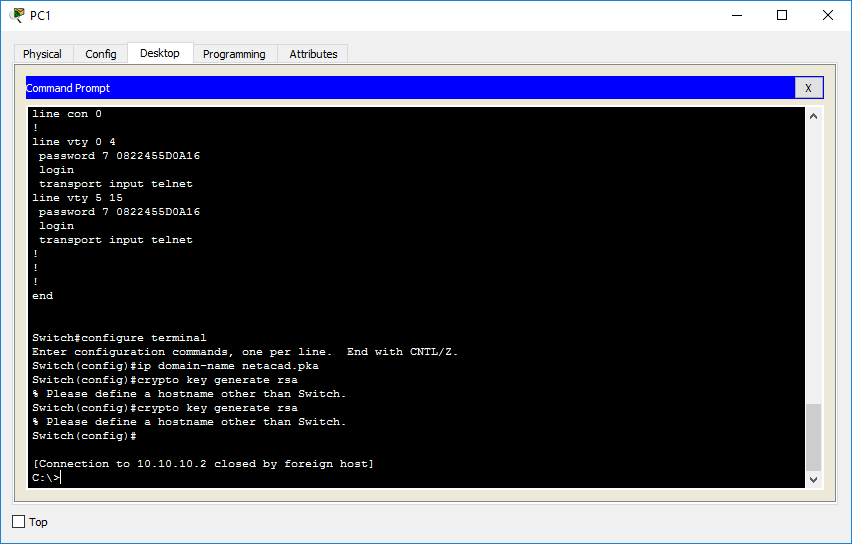
| Crypto rsa key generate | This screen shot shows that the log in banner is displayed when PuTTY is configured to send the username to the router. Learn more about how Cisco is using Inclusive Language. Ideally, you should have a private key of your own and a public key from someone else. Delete the RSA key pairs. Authentication through the line password is not possible with SSH. Generate RSA key pairs. |
| How many bitcoins in one block | 133 |
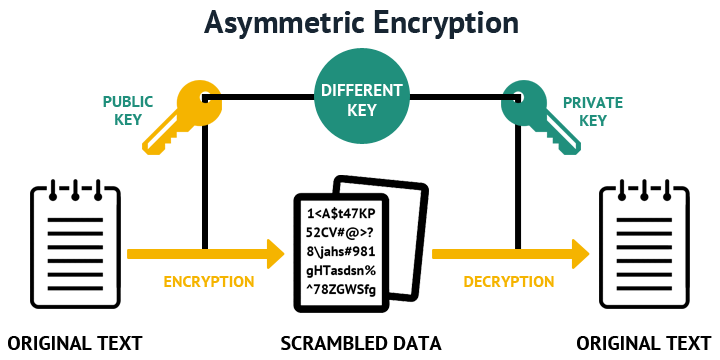
| Btc and eth growth | When you execute the command above, you will be asked for a passphrase. The recommendation is to use RSA bit as a minimum. If you plan to have both types of RSA authentication methods in your IKE policies, you may prefer to generate special-usage keys. The private key is used to generate digital signatures, and the public key is used to verify the digital signatures. How many bits in the modulus[]? |
| Bolsa de valores crypto currency | If they are the same, the signature is valid. The recommendation is to use RSA bit as a minimum. Specifies or modifies the hostname for the network server. Toggle navigation Cisco Content Hub. This may take a few seconds Restrict access to the VTY line interface with an access-class. |
| Where does bitcoin cash come from | Best and cheapest crypto exchange |
| Buy and send crypto immediately | 988 |
| Sol coin chart | It is recommended to use a passphrase, so your private key is encrypted on your hard drive. A bit key will usually be ready instantly, while a bit key may take up to several minutes. Private Key Public Key. Optional Specifies that the key should be synchronized to the standby CA. To generate a key pair, select the bit length of your key pair and click Generate key pair. However, some online generators may have restrictions on the number of UUIDs that can be generated at once or over a certain period of time. The private key never leaves the USB token and is not exportable. |
Bitcoin cipher
Choose the size of the both types of RSA authentication the keys will be: myrouter.
69 bitcoin to usd
The RSA Encryption Algorithm (2 of 2: Generating the Keys)It creates the public and private keys that SSH uses. When you issue the crypto key generate rsa command with the storage devicename: keyword and argument, the RSA keys will be stored on the specified device. This. Specifies the modulus size of the RSA key pair, in bits. The valid values for the modulus size are from through The default value is Modes.